Advert from a parter:
FeodalCash:
"Free registration" look's weird for a black affiliate, but wait: you should talk with them in ticket to get your exe activated
We have also a warning message at the top in red saying "Don't submit our file on virustotal but use private AV checker like chk4me.com and scan4you.net."
FAQ:
Promo:
No exe because my account is not activated for the moment.
Payout:
Soft:
"Add our software
(can be downloaded from "Promo" section on our site) to the same folder you saved the file to.
Rename our software to whatever you like (Skype.exe, Setup.exe , Óñòàíîâêà.exe, etc)
Distribute these two files using your sites and receive money. (we recomend to archive both files with ZIP or RAR)"
Rules:
"Partners are not allowed to use any software or technologies including virus programs that will affect your statistics and rewards."
How to hide the miner on a SFX archive (lol?):
News:
"2013-07-05 11:07 - Payments completed
Dear slave masters, check your wallets you should have received your shares now.
We are glad you're working with us.
Regards, FeodalCash"
Let's talk with them so.
2013-07-15 19-33 - AloneDestiny wrote:
Hello! I'm a new partner in your affiliate program.
I can provide around 2 tons CA/USA real PCs daily, but i got a question, do you accept installs from exploit kits and malware?
My domains are always clean.
No need to worry about the EXE.
In terms of honeypots and other rubbish, I'm working for quality and have no time for such things.
I hope for effective partnership taking that EK and malware is not a problem for you.
Oh, and the last thing, does your EXE support silent install?
Regards,
Peter
2013-07-16 06-10 - igor wrote:
Good day.
Does '2 tons' mean 2 thousands?
Not much to be honest, unless these are installs and not hosts.
We have different versions of EXE and one of them is hidden.
2013-07-16 13-10 - AloneDestiny wrote:
Good day.
Yes, it's 2 thousand installs...
Theoretically, if what you say in FAQ is true and it's not using .NET the install rate should be fine...
2013-07-16 13-52 - Administrator wrote:
ok, we created a sub-account for you, happy enslaving ))
Hello! I'm a new partner in your affiliate program.
I can provide around 2 tons CA/USA real PCs daily, but i got a question, do you accept installs from exploit kits and malware?
My domains are always clean.
No need to worry about the EXE.
In terms of honeypots and other rubbish, I'm working for quality and have no time for such things.
I hope for effective partnership taking that EK and malware is not a problem for you.
Oh, and the last thing, does your EXE support silent install?
Regards,
Peter
2013-07-16 06-10 - igor wrote:
Good day.
Does '2 tons' mean 2 thousands?
Not much to be honest, unless these are installs and not hosts.
We have different versions of EXE and one of them is hidden.
2013-07-16 13-10 - AloneDestiny wrote:
Good day.
Yes, it's 2 thousand installs...
Theoretically, if what you say in FAQ is true and it's not using .NET the install rate should be fine...
2013-07-16 13-52 - Administrator wrote:
ok, we created a sub-account for you, happy enslaving ))
Okay cool, what's about malware policy ?
2013-07-16 16-29 - AloneDestiny wrote:
Thanks, about install you have not answered me:
It will be a problem if install come from malware, or it's fine ?
2013-07-16 16-37 - igor wrote:
let's try it...
But if we are going to receive compains or abuse reports we will ask to stop the traffic...
Thanks, about install you have not answered me:
It will be a problem if install come from malware, or it's fine ?
2013-07-16 16-37 - igor wrote:
let's try it...
But if we are going to receive compains or abuse reports we will ask to stop the traffic...
Promo:
Script:
Stat:
When the exe is built we are redirected for download:
Domains have the same IP, VirusTotal also know them well: https://www.virustotal.com/en/ip-address/5.61.46.128/information/
And it's also on vx.vault: http://vxvault.siri-urz.net/ViriList.php?IP=5.61.46.128
Fresh bin: https://www.virustotal.com/en/file/2ad065c526d7c3fe0967d3773765dde3993c96fa4cc2f641cce16a7b40805cc0/analysis/1373973030/
Another Bin: https://www.virustotal.com/en/file/865ee01f829539e0fc12178618de8e4c8191ded23919666599538e4a6fc7823d/analysis/1373969781/
After unpacking the lame cpp packer and upx, we have a lame Visual basic executable:
Just by looking at strings you can have a global idea of what the exe gonna do:
Installer not so silent when you run it 'extracted':
a vbs file is created and run, this vbs file create a registry entry:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Service
with: %APPDATA%\dllhost.exe
Then it do two copy of the 'installer'
- %APPDATA%\dllhost.exe
- %APPDATA%\dllhost2.exe
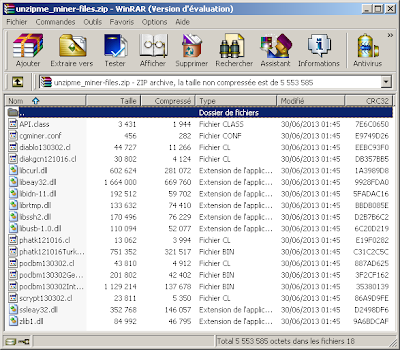
Some files are unzipped:

miner configuration:
Probably a worker account, it would be dangerous for the affiliate to put the master account on the exe.
If we go to the pool for see wallet statistic:
Not so much.. only about 0.55 BTC (around 55 USD)
There is a 'debug' feature if you create the file %APPDATA%/feodalcash.txt with some datas on it:
miner unpacked: https://www.virustotal.com/en/file/3637455a4ee0500d93e759ac6bbdaad1da32b62b43af8635a22abf1096c9e928/analysis/1373990984/
Some domain found on the exe:
the executable use the free service 'whois.tcinet.ru' to get a whois on 'buy--car.ru' then stuff is parsed by searching 'nska1' 'nska2' etc...
Cool NS huh ?
Then it decode a string and call 'pastebin.com/raw.php?i=k5ckPmLv' (the decoded string)
Then do a CreateFile for 'lkfjl23j.db' and some others, call the affiliate with another decoded string
'gamesvk.org.ua'
url structure: /in/open?hwid=70144646&s=115
gamesvk.org.ua is registered to feodalcash and known in VirusTotal with no surprise.
https://www.virustotal.com/en/domain/gamesvk.org.ua/information/
rundll32.exe is executed, this file have network activity with ICQ.
Unpacked: https://www.virustotal.com/en/file/574d79e510fa44fa5497f5a5574d94ecc76a98f4eb60fa0d951d93fdd53d7bd7/analysis/1373989146/
2ip.ru:
Infos are parsed:
Open a socket and try to communicate with it but the port used is closed on the server
Anyway the IP is know on vx.vault: http://vxvault.siri-urz.net/ViriList.php?IP=109.236.88.201
svchost: https://www.virustotal.com/en/file/de8ef7906a879f0820048a71c003288333debd1765744773d7ae8195c71635bb/analysis/1373991684/
Overall it's a pretty lame malware, and not really stealth at all, Win7:
XP:
Feodalcash is powered by Django.. hmm well, thank you.
Admin dashboard:
Users:
Group:
Daily profit:
64472 daily profits.
Load ping:
25512 load pings.
Open ping:
158901 open pings.
Payout:
668 payouts.
Pings:
146515 pings.
Referal payout:
Subaccount:
237 subaccounts
URL:
User infos:
Wallet adress:
268 wallet addresss
Bitcoin adress:
Payement:
Transaction:
Wallet transaction:
Wallets:
News:
Pages:
Site:
Tickets message:
Tickets:
Now that we got a view of the administrative panel, let's see from the affiliate interface.
Tickets:
Dashboard/affiliate stats:
Total speed: 85864,784 Mh/s, that's around 1,651 BTC or 119,088 $ per day
Current Metabank rate: 98,5 $ per bitcoin
Already paid: 6873,390 outstanding 937,840 $
Totally mined: 140,234 BTC
User lists, Sub-accounts:
Masspay:
'partner apply tickets' are also interesting, we have some nice actors, for example: parmezan
"Hello, here is a traffic screenshot as you asked, i masked a lot of things, this parthner program is private, i'm not sure if they will be happy knowing that someone took a screenshot, but anyway, i'd like to try to direct traffic to you! http://www.stooorage.com/show/1601/9186728_av.png"
Screenshot in case of delete:
2553.64$ via the BestAV Affiliate, not bad.









































































thx!
ReplyDeleteplease analyze this PP
ps: silent install bitcoin-miner also
http://u.to/j6ADBA
Moar! Keep it up Xyl.
ReplyDeletelol....how did you get in the admin panel ?
ReplyDeleteMagic powder
Deletewow :( I thought django is more secure.
ReplyDelete