Almost FUD, detected by NOD32 and Kaspersky. (2/44)
Crypted with a dirty DotNet crap
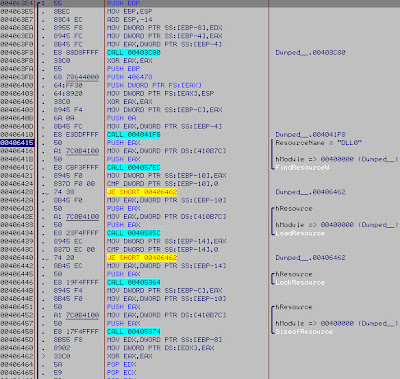
Once unpacked it's another story (33/44)
Read the ressources DLL0/1/2 and CFG
Get the config.
Do some registry shit, parse the config url get the pc name...
Call the gate.
Furtivity fail:
Wait order:
Call the gate each 2 minute for order
Order:
Retrieve and execute:
Return mode=3 to says order is done
Task complete.
Umbra thread:
Login:
Dashboard:
Start:
File upload:
Install:
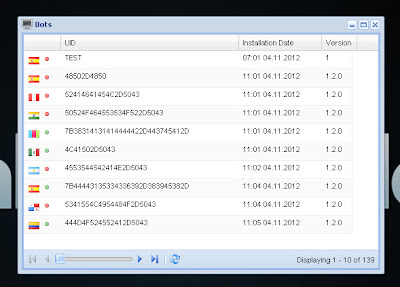
Bots:
Commands:
Country statistics:
Cpanel:
Botnet hosted on reliahost.net, they are know for hosting malwares, warez and porn.
ReliaHost website:
Unbra Loader builder:
Builder MD5: 91eda4acfb9da021d4f7b91e780b12be

































No comments:
Post a Comment