Java Web Start 2012 exploit:

Schem about alexudakov (not really searched)
3.1 changelog translated by EP_X0FF
We are pleased to present new version of pack 3.1!
-----------v3.1------------------------------------
[+]Added new JAVA ATOMIC exploit of JRE 1.6.0-1.6.0_30, 1.7.0-1.7.0_2 for FF/IE/OPERA. Sufficiently increased exploitation success.
[+]JAVA TC and JAVA RHINO combined in one .jar file
[+]added 4 activation variants:
1)JAVA with version determination, PDF with version determination before load
2)JAVA without version determination, PDF with version determination before load
3)JAVA with version determination, PDF without version determination before load
4)JAVA without version determination, PDF with version determination before load
This flexible system allows for longer not to kill traffic sources (actual for iframe traffic) or conversely with little sacrifice of traffic sources raise exploitation success (actual for Pop up traffic)
[+]The exploits delivery chain has been rewritten to be up to date, has been removed JAVA SMB, JAVA TRUST, FLASH 10 because they are no longer actual. As a consequence, there was easy to configure and install - no-Apache on port 8080 and SMB configs.
-----------v3.1------------------------------------
[+]Added new JAVA ATOMIC exploit of JRE 1.6.0-1.6.0_30, 1.7.0-1.7.0_2 for FF/IE/OPERA. Sufficiently increased exploitation success.
[+]JAVA TC and JAVA RHINO combined in one .jar file
[+]added 4 activation variants:
1)JAVA with version determination, PDF with version determination before load
2)JAVA without version determination, PDF with version determination before load
3)JAVA with version determination, PDF without version determination before load
4)JAVA without version determination, PDF with version determination before load
This flexible system allows for longer not to kill traffic sources (actual for iframe traffic) or conversely with little sacrifice of traffic sources raise exploitation success (actual for Pop up traffic)
[+]The exploits delivery chain has been rewritten to be up to date, has been removed JAVA SMB, JAVA TRUST, FLASH 10 because they are no longer actual. As a consequence, there was easy to configure and install - no-Apache on port 8080 and SMB configs.
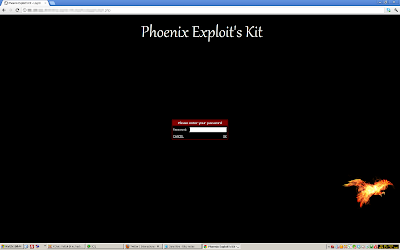
Login:
Simple statistics:
Advenced statistics:
Countries statistics:
Referers statistics:
Sources statistics:
Clear statistics:
Upload .exe:
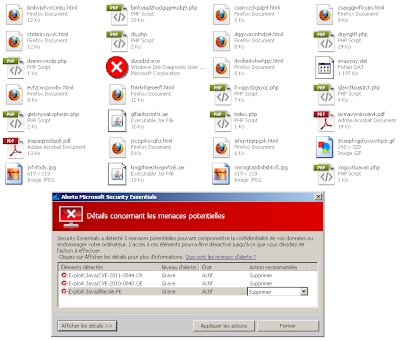
Dumped files, CVE-2010-0094 detected as Blacole.FK by MSE.
Phoenix landing:
Part of the code, looking for the os version
Welcome to our show... hack the planet
(`id`, `user_name`, `pass_hash`, `money`, `activated`) VALUES ('588', 'alexudakov', 'd8228ee30f409166ff72ecf6642ad9fc', '0.00', '0');
(`user_id`, `icq`, `email`) VALUES ('588', '', 'andrey89@nextmail.ru');
(`user_id`, `icq`, `email`) VALUES ('588', '', 'andrey89@nextmail.ru');













Very informative, thank you.
ReplyDeleteHow wierd is not that, how can you maintain access like that ? : )
ReplyDeleteHa-ha, more info here
ReplyDeletehttp://webcache.googleusercontent.com/search?q=cache:4poH_rngymkJ:dawhois.com/ip/213.155.3.88.html+andrey89%40nextmail.ru&cd=4&hl=en&ct=clnk
person: Andrew Grazin
address: RU, Yoshkar-Ola, 48/56 Lenina str
phone: +79027180151
nic-hdl: AG841-RIPE
abuse-mailbox: andrey89@nextmail.ru
Excelent!!!
ReplyDelete