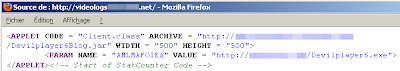
Let's check the source code:

Sort of SFX archive, 0/43 on VT, cool.
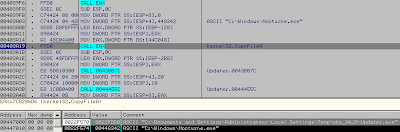
Two exe files are extracted in %TEMP%/ckz_X6J3/
Updater.exe...
--------
1) Autoreplic:
2) Create .bat file for disable the Windows firewall problem
3) Prepare a html file
4) Create and +h a log file
5) Create and fill the html file
6) Prepare a core.bat file
7) Prepare a java.sys file (what a joke ?)
8) finish the java.sys creation and +h it, create a java.bat file and exec it
9) keylog, save the html file and send it to the ftp
10) Pwning
I've jumped some steps like the creation of 'list.log' who contain running process, the screenshot features and some others stuff :þ
It's another 'easy' sample for start into malware reversing for see "what's he do", "how that work"
The code is clear and not hardcoded.
MD5 ~ e7888818481b3ff5feaa6f4e63201486
Have fun.










No comments:
Post a Comment